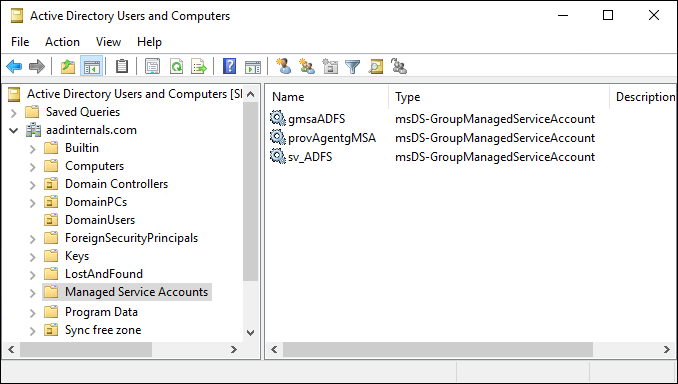
Exfiltrating NTHashes by abusing Microsoft Entra Domain Services
Last year I gave a presentation titled Dumping NTHashes from Azure AD at TROOPERS conference.
The talk was about how the Microsoft Entra Domain Services (formerly Azure AD Domain Services) works and how it enabled dumping NTHashes from Entra ID (formerly Azure AD).
In this blog, I’ll show how Microsoft Entra Domain Services (MEDS) can be (ab)used to exfiltrate NTHashes from on-prem Active Directory.