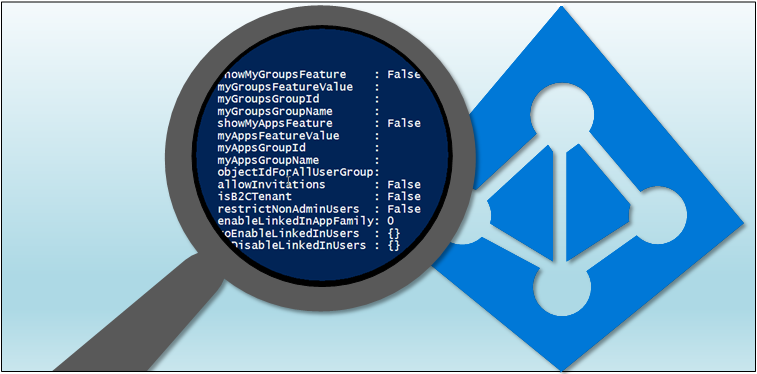
AAD Kill chain
imageMapResize(); Introduction According to Verizon’s Data Breach Investigations Report 2020, externals attackers are considerable more common than internal attackers. In the cloud era, attacking the organisation from the outside is much more difficult, if not impossible. Therefore, to be able to access organisation’s data, one must gain some level of legitimate access to the organisation.
The Azure AD and Microsoft 365 kill chain is a collection of recon techniques and hacking tools I’ve discovered and built during the last 10+ years while working with Microsoft cloud services.