Spoofing Azure AD sign-ins logs by imitating AD FS Hybrid Health Agent
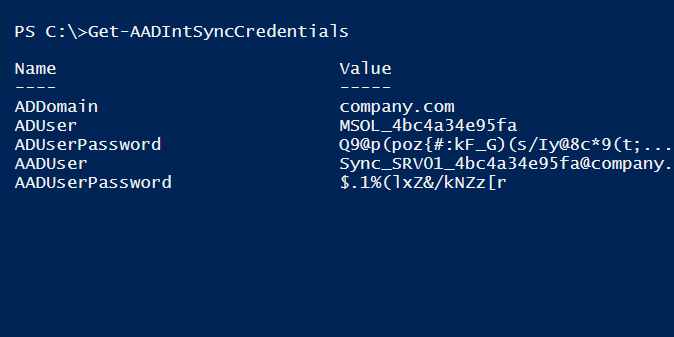
Azure AD Connect Health is a feature that allows viewing the health of on-prem hybrid infrastructure components, including Azure AD Connect and AD FS servers. Health information is gathered by agents installed on each on-prem hybrid server. Since March 2021, also AD FS sign-in events are gathered and sent to Azure AD.
In this write-up (based on a Threat Analysis report by Secureworks), I’ll explain how anyone with a local administrator access to AD FS server (or proxy), can create arbitrary sign-ins events to Azure AD sign-ins log. Moreover, I’ll show how Global Administrators can register fake agents to Azure AD - even for tenants not using AD FS at all.